Semicolon attack
M$ IIS webserver is vulnerable to an attack using a semicolon in conjunction with benign extensions to fool it into executing malware.
Security humour
"X-Mas Capture the Flag" challenge
File recovery
Ever deleted a file by accident? Well... you don't need to be a forensics guru to reclaim the deleted file.
From the genuises who created, CCleaner, comes Recuva... a portable tool that you can copy to a flash drive and insert into any machine to recover lost files. This is ideal compared to installing recovery tools as it reduces the risk of accidentally writing over files that you wish to repossess.
In my demo, my "Recycle Bin" is emptied. I launch Recuva Portable and initiate a scan of my local drive. It displays a deleted file for restoration. Upon recovery, I am able to view my original data.



You need administrative access to the target system in order to scan for deleted files. On the flip side, this exercise shows how rudimentary it is to recover files and thus you need to protect your privacy by wiping files that you no longer need. Eraser is the solution for you.

From the genuises who created, CCleaner, comes Recuva... a portable tool that you can copy to a flash drive and insert into any machine to recover lost files. This is ideal compared to installing recovery tools as it reduces the risk of accidentally writing over files that you wish to repossess.
In my demo, my "Recycle Bin" is emptied. I launch Recuva Portable and initiate a scan of my local drive. It displays a deleted file for restoration. Upon recovery, I am able to view my original data.



You need administrative access to the target system in order to scan for deleted files. On the flip side, this exercise shows how rudimentary it is to recover files and thus you need to protect your privacy by wiping files that you no longer need. Eraser is the solution for you.

NeXpose Metasploit integration
 With Rapid7's funding of Metasploit, both NeXpose and Metasploit are seamlessly integrated to automatically scan and remotely exploit target machines. Far out!!! I ran the plugin to successfully exploit my vulnerable virtual machine.
With Rapid7's funding of Metasploit, both NeXpose and Metasploit are seamlessly integrated to automatically scan and remotely exploit target machines. Far out!!! I ran the plugin to successfully exploit my vulnerable virtual machine.
NeXpose vs Nessus
I've used Nessus for years. I only recently heard of NeXpose after Rapid7 started funding Metasploit and promised to integrate their scanner with Metasploit. I decided to give NeXpose a whirl. The learning curve wasn't steep when using the scanner.
Scanned the same target machine with Nessus.
The 2 scanners produce the same result but I always believe in the need to use multiple tools to assess vulnerabilities in infrastructures, networks, systems and applications to uncover the full state of insecurity.
Scanned the same target machine with Nessus.
The 2 scanners produce the same result but I always believe in the need to use multiple tools to assess vulnerabilities in infrastructures, networks, systems and applications to uncover the full state of insecurity.
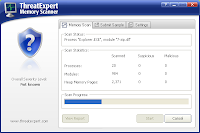
ThreatExpert
Found out about this resource from attending a Symantec security seminar today. ThreatExpert provides a list of free services including a "Memory Scanner". This tool scans your memory for malware. Users can submit suspicious files for analysis to discover the file's behaviour without having to execute it.







Code injection via English text?
Session video recording vs keystroke logging
Visually, it is easier to comprehend what is occurring during a session when reviewing a recording as compared to keystrokes. However, recordings consume a lot of storage and cannot be indexed for easy searching unlike keylogging. Session video recording is more secure as it does not record the privilege password. It is also less intrusive because no software or tweaking is required on the endpoint system.
The jury is still out on session video recording. It is a good concept but its disadvantages currently outweigh its benefits.
The jury is still out on session video recording. It is a good concept but its disadvantages currently outweigh its benefits.
Network forensics puzzle #2
My answer to the new digital forensics puzzle. I ran "ngrep" in Ubuntu to search for lines containing the "@" symbol. Ann's email address is "sneakyg33k@aol.com". Her secret lover's email address is "mistersecretx@aol.com". She requests him to bring his fake passport and bathing suit.
Searching for strings matching "aol.com" reveals "AUTH=LOGIN". I locate the login sequence in Wireshark.
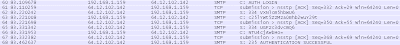 I figure that the string "VXNlcm5hbWU6" is encoded and has signficance. Googling this string reveals that it is "Username:" encoded in Base64. I use the "Enocde/Hash" tool in Paros (Windows) to confirm this fact. Lo and behold! I start to decode the other encoded strings to reveal the password "558r00lz".
I figure that the string "VXNlcm5hbWU6" is encoded and has signficance. Googling this string reveals that it is "Username:" encoded in Base64. I use the "Enocde/Hash" tool in Paros (Windows) to confirm this fact. Lo and behold! I start to decode the other encoded strings to reveal the password "558r00lz".




To locate the attachment that Ann sent, I search for the string "Content-Type:". The name of the attachment is "secretrendezvous.docx". I usually like to challenge myself by manually carving out file transfers but in this specific case, I was unsuccessful. Using file carvers like "tcpxtract" and "Foremost" also resulted in failure. I resorted to using NetMiner (Windows) to acquire this file.
 I do not have Office 2007 installed on my laptop. I decided to be creative and viewed the file in Google Docs to reveal their secret meeting place. The MD5 hash of this file is "9e423e11db88f01bbff81172839e1923". To access the embedded image, I rename the extension ".docx" to ".zip". I am able to access the image from the "/word/media/" folder. The MD5 hash of this image is "aadeace50997b1ba24b09ac2ef1940b7".
I do not have Office 2007 installed on my laptop. I decided to be creative and viewed the file in Google Docs to reveal their secret meeting place. The MD5 hash of this file is "9e423e11db88f01bbff81172839e1923". To access the embedded image, I rename the extension ".docx" to ".zip". I am able to access the image from the "/word/media/" folder. The MD5 hash of this image is "aadeace50997b1ba24b09ac2ef1940b7".


Searching for strings matching "aol.com" reveals "AUTH=LOGIN". I locate the login sequence in Wireshark.
 I figure that the string "VXNlcm5hbWU6" is encoded and has signficance. Googling this string reveals that it is "Username:" encoded in Base64. I use the "Enocde/Hash" tool in Paros (Windows) to confirm this fact. Lo and behold! I start to decode the other encoded strings to reveal the password "558r00lz".
I figure that the string "VXNlcm5hbWU6" is encoded and has signficance. Googling this string reveals that it is "Username:" encoded in Base64. I use the "Enocde/Hash" tool in Paros (Windows) to confirm this fact. Lo and behold! I start to decode the other encoded strings to reveal the password "558r00lz".



To locate the attachment that Ann sent, I search for the string "Content-Type:". The name of the attachment is "secretrendezvous.docx". I usually like to challenge myself by manually carving out file transfers but in this specific case, I was unsuccessful. Using file carvers like "tcpxtract" and "Foremost" also resulted in failure. I resorted to using NetMiner (Windows) to acquire this file.
 I do not have Office 2007 installed on my laptop. I decided to be creative and viewed the file in Google Docs to reveal their secret meeting place. The MD5 hash of this file is "9e423e11db88f01bbff81172839e1923". To access the embedded image, I rename the extension ".docx" to ".zip". I am able to access the image from the "/word/media/" folder. The MD5 hash of this image is "aadeace50997b1ba24b09ac2ef1940b7".
I do not have Office 2007 installed on my laptop. I decided to be creative and viewed the file in Google Docs to reveal their secret meeting place. The MD5 hash of this file is "9e423e11db88f01bbff81172839e1923". To access the embedded image, I rename the extension ".docx" to ".zip". I am able to access the image from the "/word/media/" folder. The MD5 hash of this image is "aadeace50997b1ba24b09ac2ef1940b7".

My new article
Password length
Interesting statistics but I wonder how reliable the source is. It is fascinating the difference and benefits that passwords with a length of 12 yields over those with 11.
Client-side validation
One of the rules of application security is to never implement client-side validation but rely on server-side validation.
I came across an e-card greeting on the "Uniquely Singapore" website and decided to try it out. Hmmmm... the form doesn't allow me to submit an e-card with the recipient and sender emails being the same. Did they implement client-side validation? I decided to disable Javascript in Firefox. I reload the webpage and resubmit. Viola!!! Email sent and received.






This confirms that Javascript is used to validate submissions on the client's machine. The secure way would be to validate on the server so that the client cannot manipulate requests to successfully bypass validation.
I came across an e-card greeting on the "Uniquely Singapore" website and decided to try it out. Hmmmm... the form doesn't allow me to submit an e-card with the recipient and sender emails being the same. Did they implement client-side validation? I decided to disable Javascript in Firefox. I reload the webpage and resubmit. Viola!!! Email sent and received.






This confirms that Javascript is used to validate submissions on the client's machine. The secure way would be to validate on the server so that the client cannot manipulate requests to successfully bypass validation.
Zbot
Downloaded a sample of "Zbot" from Offensive Computing's site. I'm no reverse engineering guru but decided to give it a go at analysing this nasty piece of malware. Fired up "Regshot" to detect modifications made to my virtual machine.
The following registry keys were added.
HKLM\SOFTWARE\Classes\.exe HKLM\SOFTWARE\Classes\.exe \PersistentHandler HKLM\SOFTWARE\Microsoft\DownloadManager HKLM\SOFTWARE\XTB
Corresponding values that were added.
HKLM\SOFTWARE\Classes\.exe \PersistentHandler\: "{098f2470-bae0-11cd-b579-08002b30bfeb}"
HKLM\SOFTWARE\Classes\.exe \: "exefile"
HKLM\SOFTWARE\Classes\.exe \Content Type: "application/x-msdownload" HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Windows: "C:\WINDOWS\explorer.exe "
HKLM\SOFTWARE\XTB\httpaddr: "http://server.xyz/drss,jpg"
HKLM\SOFTWARE\XTB\xintr: "1440"
HKLM\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List\C:\WINDOWS\explorer.exe : "C:\WINDOWS\explorer.exe :*:Enabled:explorer"
HKLM\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List\C:\WINDOWS\explorer.exe : "C:\WINDOWS\explorer.exe :*:Enabled:explorer"
HKU\.DEFAULT\Software\Microsoft\Windows\ShellNoRoam\MUICache\C:\WINDOWS\explorer.exe : "explorer"
HKU\S-1-5-21-299502267-448539723-839522115-1003\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyEnable: 0x00000000
HKU\S-1-5-21-299502267-448539723-839522115-1003\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\DefaultConnectionSettings: 3C 00 00 00 02 00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 04 00 00 00 00 00 00 00 10 8A 55 3E 84 54 CA 01 01 00 00 00 C0 A8 DC 89 00 00 00 00 00 00 00 00
HKU\S-1-5-21-299502267-448539723-839522115-1003\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\SavedLegacySettings: 3C 00 00 00 02 00 00 00 09 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
HKU\S-1-5-21-299502267-448539723-839522115-1003\Software\Microsoft\Windows\ShellNoRoam\MUICache\C:\Documents and Settings\tester\Desktop\malware.exe: "malware"
HKU\S-1-5-21-299502267-448539723-839522115-1003\Software\Microsoft\Windows\ShellNoRoam\MUICache\C:\WINDOWS\explorer.exe : "explorer"
HKU\S-1-5-18\Software\Microsoft\Windows\ShellNoRoam\MUICache\C:\WINDOWS\explorer.exe : "explorer"
The following files were added.
C:\WINDOWS\Prefetch\EXPLORER.EXE -2F6C44D8.pf
C:\WINDOWS\Prefetch\MALWARE.EXE-17DA0AE5.pf
C:\WINDOWS\Prefetch\RUNDLL32.EXE-4912BB30.pf
C:\WINDOWS\system32\wbem\Logs\wmiprov.log
C:\WINDOWS\explorer.exe
Files were modified.
C:\Documents and Settings\tester\Cookies\index.dat
C:\Documents and Settings\tester\Local Settings\History\History.IE5\index.dat
C:\Documents and Settings\tester\Local Settings\Temporary Internet Files\Content.IE5\index.dat
C:\Documents and Settings\tester\ntuser.dat.LOG
C:\WINDOWS\system32\config\default.LOG
C:\WINDOWS\system32\config\software
C:\WINDOWS\system32\config\software.LOG
C:\WINDOWS\system32\config\system.LOG
As seen by the registry values added, the malware creates a backdoor into the victim's system. A pop-up was triggered by the malware and by clicking on "Unblock", the hacker has access to the system by adding a permit rule in "Windows Firewall". 2 Explorer processes can be seen from "Task Manager". The malware creates a file "explorer.exe " in "C:\Windows". Note that the fake Explorer does not replace the authentic one native in Windows because the hacker adds a space behind the extension. 2 Explorer processes are seen in "Task Manager" and one of them is the backdoor. "Active Ports" and "netstat" (with the -nab switch) confirm that the backdoor listens on TCP port 113 and UDP port 1025.



The malware requests a fake resource, drss,jpg, from a server presumably controlled by the hacker. This is not a typo as the hacker intentionally uses a comma instead of a fullstop. I hypothesize that the hacker uses this fake request to capture the victim's IP address so that he knows which IP address to connect to.


Besides "0wning" bots, I believe that the hacker is after the victim's surfing history and logs based on the files modified.
Launched "Capture BAT" to verify the findings from "Regshot". "Capture BAT" confirms that the same registry keys and values were added. It also confirms the spawning of the fake Explorer process. The packet capture by "Capture BAT" also confirms the HTTP request to "server.xyz".

The following registry keys were added.
HKLM\SOFTWARE\Classes\.exe HKLM\SOFTWARE\Classes\.exe \PersistentHandler HKLM\SOFTWARE\Microsoft\DownloadManager HKLM\SOFTWARE\XTB
Corresponding values that were added.
HKLM\SOFTWARE\Classes\.exe \PersistentHandler\: "{098f2470-bae0-11cd-b579-08002b30bfeb}"
HKLM\SOFTWARE\Classes\.exe \: "exefile"
HKLM\SOFTWARE\Classes\.exe \Content Type: "application/x-msdownload" HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\Windows: "C:\WINDOWS\explorer.exe "
HKLM\SOFTWARE\XTB\httpaddr: "http://server.xyz/drss,jpg"
HKLM\SOFTWARE\XTB\xintr: "1440"
HKLM\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List\C:\WINDOWS\explorer.exe : "C:\WINDOWS\explorer.exe :*:Enabled:explorer"
HKLM\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List\C:\WINDOWS\explorer.exe : "C:\WINDOWS\explorer.exe :*:Enabled:explorer"
HKU\.DEFAULT\Software\Microsoft\Windows\ShellNoRoam\MUICache\C:\WINDOWS\explorer.exe : "explorer"
HKU\S-1-5-21-299502267-448539723-839522115-1003\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ProxyEnable: 0x00000000
HKU\S-1-5-21-299502267-448539723-839522115-1003\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\DefaultConnectionSettings: 3C 00 00 00 02 00 00 00 01 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 04 00 00 00 00 00 00 00 10 8A 55 3E 84 54 CA 01 01 00 00 00 C0 A8 DC 89 00 00 00 00 00 00 00 00
HKU\S-1-5-21-299502267-448539723-839522115-1003\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections\SavedLegacySettings: 3C 00 00 00 02 00 00 00 09 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
HKU\S-1-5-21-299502267-448539723-839522115-1003\Software\Microsoft\Windows\ShellNoRoam\MUICache\C:\Documents and Settings\tester\Desktop\malware.exe: "malware"
HKU\S-1-5-21-299502267-448539723-839522115-1003\Software\Microsoft\Windows\ShellNoRoam\MUICache\C:\WINDOWS\explorer.exe : "explorer"
HKU\S-1-5-18\Software\Microsoft\Windows\ShellNoRoam\MUICache\C:\WINDOWS\explorer.exe : "explorer"
The following files were added.
C:\WINDOWS\Prefetch\EXPLORER.EXE -2F6C44D8.pf
C:\WINDOWS\Prefetch\MALWARE.EXE-17DA0AE5.pf
C:\WINDOWS\Prefetch\RUNDLL32.EXE-4912BB30.pf
C:\WINDOWS\system32\wbem\Logs\wmiprov.log
C:\WINDOWS\explorer.exe
Files were modified.
C:\Documents and Settings\tester\Cookies\index.dat
C:\Documents and Settings\tester\Local Settings\History\History.IE5\index.dat
C:\Documents and Settings\tester\Local Settings\Temporary Internet Files\Content.IE5\index.dat
C:\Documents and Settings\tester\ntuser.dat.LOG
C:\WINDOWS\system32\config\default.LOG
C:\WINDOWS\system32\config\software
C:\WINDOWS\system32\config\software.LOG
C:\WINDOWS\system32\config\system.LOG
As seen by the registry values added, the malware creates a backdoor into the victim's system. A pop-up was triggered by the malware and by clicking on "Unblock", the hacker has access to the system by adding a permit rule in "Windows Firewall". 2 Explorer processes can be seen from "Task Manager". The malware creates a file "explorer.exe " in "C:\Windows". Note that the fake Explorer does not replace the authentic one native in Windows because the hacker adds a space behind the extension. 2 Explorer processes are seen in "Task Manager" and one of them is the backdoor. "Active Ports" and "netstat" (with the -nab switch) confirm that the backdoor listens on TCP port 113 and UDP port 1025.



The malware requests a fake resource, drss,jpg, from a server presumably controlled by the hacker. This is not a typo as the hacker intentionally uses a comma instead of a fullstop. I hypothesize that the hacker uses this fake request to capture the victim's IP address so that he knows which IP address to connect to.


Besides "0wning" bots, I believe that the hacker is after the victim's surfing history and logs based on the files modified.
Launched "Capture BAT" to verify the findings from "Regshot". "Capture BAT" confirms that the same registry keys and values were added. It also confirms the spawning of the fake Explorer process. The packet capture by "Capture BAT" also confirms the HTTP request to "server.xyz".

Google warning
Google now warns its users of sites with malicious content. Google displayed a warning when I searched for the URL of my toy supplier. It also blocked my access to the suspect site.




Microsoft Security Essentials
M$ released a free AV called "Security Essentials" for home consumers. I gave it a test drive and found it intuitive to manage as well as use.


I tested it against the malicious MP3 file that I analysed previously and "Security Essentials" effortlessly detected the malware instantaneously. Avast! on the other hand needed me to manually trigger a scan before it warned me of the presence of malware. 27 AV engines hosted on VirusTotal missed it.




I tested it against the malicious MP3 file that I analysed previously and "Security Essentials" effortlessly detected the malware instantaneously. Avast! on the other hand needed me to manually trigger a scan before it warned me of the presence of malware. 27 AV engines hosted on VirusTotal missed it.


2FA no longer effective?
Malware patiently waits for victims to successfully log into their online banking account using their 2 factor authentication token before proceeding to steal their money.
I'm not surprised that most AV engines can't detect Zeus. I proved previously how ineffective AV engines are against malware.
I'm not surprised that most AV engines can't detect Zeus. I proved previously how ineffective AV engines are against malware.
Flash cookies
 First, it was cookies residing on your system that could compromise your privacy. Now I read about the threat of Flash cookies??? WTH???
First, it was cookies residing on your system that could compromise your privacy. Now I read about the threat of Flash cookies??? WTH???Windows users are safe thanks to the almight Ccleaner. It wipes Flash cookies on your computer.
Ubuntu users can add the following command to "ubuntuprivacy" if you have Flash Player installed on your system.
sudo srm -rllv .macromedia/Flash_Player/#SharedObjects/
For the paranoid
I wrote a new script for the paranoid. This script will wipe your memory, swap and free space on your Ubuntu system. Please note that this is a time consuming process.
#!/bin/sh
echo "\033[0;34mProceeding to wipe your memory, swap and free space. Please be warned that this is time consuming and may take hours.\033[0m"
echo
echo "\033[0;31mWiping memory.\033[0m"
sudo smem -lv
echo "\033[0;32mMemory wiped.\033[0m"
echo "\033[0;31mWiping swap.\033[0m"
#Please run "cat /proc/swaps" to determine your mounted swap devices and customise the following line for your machine.
sudo swapoff /dev/sda5
sudo sswap -llv /dev/sda5
sudo swapon /dev/sda5
echo "\033[0;32mSwap wiped.\033[0m"
echo "\033[0;31mWiping free space.\033[0m"
sudo sfill -llv /home/
echo "\033[0;32mFree space wiped.\033[0m"
#"ubuntuparanoia" written by commandrine.
#Please send comments and queries to commandrine[at]gmail[dot]com.
#Version 1.0 dated 16th Sept 2009.
#Pre-requisite is having "secure-delete" installed. Install it using "sudo apt-get install secure-delete".
#Save this script to your home folder. Run "sudo chmod +x ubuntuparanoia.sh" to make it executable.
Download it here.
#!/bin/sh
echo "\033[0;34mProceeding to wipe your memory, swap and free space. Please be warned that this is time consuming and may take hours.\033[0m"
echo
echo "\033[0;31mWiping memory.\033[0m"
sudo smem -lv
echo "\033[0;32mMemory wiped.\033[0m"
echo "\033[0;31mWiping swap.\033[0m"
#Please run "cat /proc/swaps" to determine your mounted swap devices and customise the following line for your machine.
sudo swapoff /dev/sda5
sudo sswap -llv /dev/sda5
sudo swapon /dev/sda5
echo "\033[0;32mSwap wiped.\033[0m"
echo "\033[0;31mWiping free space.\033[0m"
sudo sfill -llv /home/
echo "\033[0;32mFree space wiped.\033[0m"
#"ubuntuparanoia" written by commandrine.
#Please send comments and queries to commandrine[at]gmail[dot]com.
#Version 1.0 dated 16th Sept 2009.
#Pre-requisite is having "secure-delete" installed. Install it using "sudo apt-get install secure-delete".
#Save this script to your home folder. Run "sudo chmod +x ubuntuparanoia.sh" to make it executable.
Download it here.
v2.0
I have modified "ubuntuprivacy" for enhanced privacy.
#!/bin/sh
echo "\033[0;34mProceeding to clean your system to ensure your privacy.\033[0m"
echo
echo "\033[0;31mWiping Firefox history and cache.\033[0m"
sudo srm -rllv .mozilla/firefox/*.default/*.sqlite
sudo srm -rllv .mozilla/firefox/*.default/Cache/*
echo "\033[0;32mFirefox history and cache wiped.\033[0m"
echo "\033[0;31mWiping Trash.\033[0m"
sudo srm -rllv .local/share/Trash/
echo "\033[0;32mTrash wiped.\033[0m"
echo "\033[0;31mWiping Applications history and cache.\033[0m"
sudo srm -rllv .recently-used
sudo srm -rllv .recently-used.xbel
sudo srm -rllv .thumbnails
sudo srm -rllv .openoffice.org/*/user/temp
sudo srm -rllv .openoffice.org/*/user/backup
sudo srm -rllv .purple/logs/*/*
sudo srm -rllv .xsession-errors
sudo srm -rllv .gimp-*/tmp
echo "\033[0;32mApplications history wiped.\033[0m"
#"ubuntuprivacy" written by commandrine.
#Please send comments and queries to commandrine[at]gmail[dot]com.
#Version 2.0 dated 14th Sept 2009.
#Pre-requisite is having "secure-delete" installed. Install it using "sudo apt-get install secure-delete".
#Save this script to your home folder. Run "sudo chmod +x ubuntuprivacy.sh" to make it executable.
Download it here.
#!/bin/sh
echo "\033[0;34mProceeding to clean your system to ensure your privacy.\033[0m"
echo
echo "\033[0;31mWiping Firefox history and cache.\033[0m"
sudo srm -rllv .mozilla/firefox/*.default/*.sqlite
sudo srm -rllv .mozilla/firefox/*.default/Cache/*
echo "\033[0;32mFirefox history and cache wiped.\033[0m"
echo "\033[0;31mWiping Trash.\033[0m"
sudo srm -rllv .local/share/Trash/
echo "\033[0;32mTrash wiped.\033[0m"
echo "\033[0;31mWiping Applications history and cache.\033[0m"
sudo srm -rllv .recently-used
sudo srm -rllv .recently-used.xbel
sudo srm -rllv .thumbnails
sudo srm -rllv .openoffice.org/*/user/temp
sudo srm -rllv .openoffice.org/*/user/backup
sudo srm -rllv .purple/logs/*/*
sudo srm -rllv .xsession-errors
sudo srm -rllv .gimp-*/tmp
echo "\033[0;32mApplications history wiped.\033[0m"
#"ubuntuprivacy" written by commandrine.
#Please send comments and queries to commandrine[at]gmail[dot]com.
#Version 2.0 dated 14th Sept 2009.
#Pre-requisite is having "secure-delete" installed. Install it using "sudo apt-get install secure-delete".
#Save this script to your home folder. Run "sudo chmod +x ubuntuprivacy.sh" to make it executable.
Download it here.
How it all started?
My passion for Information Security began when I took a module called "Internet Security" in university. It was in the lab sessions where I was first exposed to Linux, host-based firewalls, encryption, sniffing, spoofing and Trojans.
A flip was switched in my head and I realised my calling in life. I was hooked and the rest as they say is history.
A flip was switched in my head and I realised my calling in life. I was hooked and the rest as they say is history.
ubuntuprivacy
Realised that "wipefox" was too limited as it only wiped files related to Firefox usage. I wrote a new script that I named "ubuntuprivacy" to include commands to clear other traces left behind as a result of activities performed on your system.
"ubuntuprivacy" currently wipes your Firefox history and cache, Ubuntu Trash and "Recent Documents" history.
#!/bin/sh
echo “Proceeding to clean your system to ensure your privacy.”
echo “Wiping Firefox history and cache.”
sudo srm -rllv .mozilla/firefox/*.default/*.sqlite
sudo srm -rllv .mozilla/firefox/*.default/Cache/*
sudo srm -rllv .mozilla/firefox/*.default/OfflineCache/*
echo “Wiping Ubuntu Trash.”
sudo srm -rllv .local/share/Trash/files
echo “Wiping Recent Documents history.”
sudo srm -rllv .recently-used.xbel
#"ubuntuprivacy" written by commandrine.
#Please send comments and queries to commandrine[at]gmail[dot]com.
#Version 1.0 dated 12th Sept 2009.
#Pre-requisite is having "secure-delete" installed. Install it using "sudo apt-get install secure-delete".
Lazy to create the script. Download it here. More items to be tackled by this script in the near future.
"ubuntuprivacy" currently wipes your Firefox history and cache, Ubuntu Trash and "Recent Documents" history.
#!/bin/sh
echo “Proceeding to clean your system to ensure your privacy.”
echo “Wiping Firefox history and cache.”
sudo srm -rllv .mozilla/firefox/*.default/*.sqlite
sudo srm -rllv .mozilla/firefox/*.default/Cache/*
sudo srm -rllv .mozilla/firefox/*.default/OfflineCache/*
echo “Wiping Ubuntu Trash.”
sudo srm -rllv .local/share/Trash/files
echo “Wiping Recent Documents history.”
sudo srm -rllv .recently-used.xbel
#"ubuntuprivacy" written by commandrine.
#Please send comments and queries to commandrine[at]gmail[dot]com.
#Version 1.0 dated 12th Sept 2009.
#Pre-requisite is having "secure-delete" installed. Install it using "sudo apt-get install secure-delete".
SSLScan
Need to assess your SSL/TLS-enabled webserver to ensure that it is configured securely? Use SSLScan.
commandrine@bridge:~$ sslscan 10.10.10.12
It is an accurate and fast scanner. As seen in the extracted output below, it determines that my test webserver supports the weak SSLv2.
Testing SSL server 10.10.10.12 on port 443
Supported Server Cipher(s):
Accepted SSLv2 168 bits DES-CBC3-MD5
Accepted SSLv2 56 bits DES-CBC-MD5
Accepted SSLv2 40 bits EXP-RC2-CBC-MD5
Accepted SSLv2 128 bits RC2-CBC-MD5
Accepted SSLv2 40 bits EXP-RC4-MD5
Accepted SSLv2 128 bits RC4-MD5
commandrine@bridge:~$ sslscan 10.10.10.12
It is an accurate and fast scanner. As seen in the extracted output below, it determines that my test webserver supports the weak SSLv2.
Testing SSL server 10.10.10.12 on port 443
Supported Server Cipher(s):
Accepted SSLv2 168 bits DES-CBC3-MD5
Accepted SSLv2 56 bits DES-CBC-MD5
Accepted SSLv2 40 bits EXP-RC2-CBC-MD5
Accepted SSLv2 128 bits RC2-CBC-MD5
Accepted SSLv2 40 bits EXP-RC4-MD5
Accepted SSLv2 128 bits RC4-MD5
SANS network forensics contest
Sent in my submission for the SANS network forensics contest and since its past the entry deadline, I decided to post my answer.
My forensics machine of choice is a Lenovo Thinkpad T60 running Ubuntu 9.04. It has an Intel Duo Core processor with 3GB RAM. Samples of tools I have installed to facilitate network forensic analysis are: ngrep, Splunk, Wireshark, Netifera, Tcpxtract, Foremost, GHex, ssldump, etc.
I downloaded the pcap file and calculated the hash to confirm that I had the complete evidence file.
commandrine@bridge:~$ md5sum evidence.pcap
d187d77e18c84f6d72f5845edca833f5 evidence.pcap
commandrine@bridge:~$
Typically I would use ngrep to do keyword searches against large pcap files. An alternative would be running Tshark to convert the contents of large pcap files to text before using search tools like Splunk to identify clues/evidence. The Anarchy-R-Us staff mentioned that the suspect machine was only on the network for a short duration thus the rational for using Wireshark to filter out packets to and from IP 192.168.1.158 to narrow the scope instead of a more sophisticated filtering mechanism. The filter I use within Wireshark is "ip.addr==192.168.1.158".
Manually combing through the 68 displayed packets, I witness the username "sec558user1" and the first IM message "Here's the secret recipe... I just downloaded it from the file server. Just copy to a thumb drive and you're good to go >:-)".
Multiple packets with the text "Cool FileXfer" and the filename "recipe.docx" are discovered. Searching Google for the keywords "Cool FileXfer" reveals that AIM is the IM medium being used. I use the "Follow TCP Stream" feature in Wireshark to reveal the raw data related to the file transfer of "recipe.docx". The magic bytes associated with .docx files are "50 4B 03 04" or its ASCII equivalent of "PK..". I saw all the raw data from the TCP stream and save it into a file called "evidence.zip" which is coincidently also associated with the magic bytes "PK..".



Next I run "Foremost" against this file to extract out the transferred file. A zip file is extracted to the folder "sansevidence".
commandrine@bridge:~$ foremost -i evidence.zip -o sansevidence/
Processing: evidence.zip
|*|
commandrine@bridge:~$
Expanding the archive, I drill down to the folder "word", I find a file called "document.xml".


Opening the file in OpenOffice, the file reveals the following information.
Recipe for Disaster:
1 serving
Ingredients
4 cups sugar
2 cups water
In a medium saucepan, bring the water to a boil. Add sugar.
Stir gently over low heat until sugar is fully dissolved.
Remove the saucepan from heat. Allow to cool completely.
Pour into gas tank. Repeat as necessary.
Calculated the MD5 checksum of the evidence file.
commandrine@bridge:~/word$ md5sum document.xml
90ce695222b157c7148d83e19ea549f6 document.xml
commandrine@bridge:~/word$
Alternatively, I am also able to manually carve out the archive without using "Foremost". I open up the file "evidence.zip" (containing the raw data saved from Wireshark) using Ghex. I delete the ASCII values before the first instance of the ASCII values "Pk.." and delete the chunk starting with "OFT2" at the end of the file.


Once the extra bytes are removed, save the file and it can be opened using any archive management software to reveal the stolen recipe.
My forensics machine of choice is a Lenovo Thinkpad T60 running Ubuntu 9.04. It has an Intel Duo Core processor with 3GB RAM. Samples of tools I have installed to facilitate network forensic analysis are: ngrep, Splunk, Wireshark, Netifera, Tcpxtract, Foremost, GHex, ssldump, etc.
I downloaded the pcap file and calculated the hash to confirm that I had the complete evidence file.
commandrine@bridge:~$ md5sum evidence.pcap
d187d77e18c84f6d72f5845edca833f5 evidence.pcap
commandrine@bridge:~$
Typically I would use ngrep to do keyword searches against large pcap files. An alternative would be running Tshark to convert the contents of large pcap files to text before using search tools like Splunk to identify clues/evidence. The Anarchy-R-Us staff mentioned that the suspect machine was only on the network for a short duration thus the rational for using Wireshark to filter out packets to and from IP 192.168.1.158 to narrow the scope instead of a more sophisticated filtering mechanism. The filter I use within Wireshark is "ip.addr==192.168.1.158".
Manually combing through the 68 displayed packets, I witness the username "sec558user1" and the first IM message "Here's the secret recipe... I just downloaded it from the file server. Just copy to a thumb drive and you're good to go >:-)".
Multiple packets with the text "Cool FileXfer" and the filename "recipe.docx" are discovered. Searching Google for the keywords "Cool FileXfer" reveals that AIM is the IM medium being used. I use the "Follow TCP Stream" feature in Wireshark to reveal the raw data related to the file transfer of "recipe.docx". The magic bytes associated with .docx files are "50 4B 03 04" or its ASCII equivalent of "PK..". I saw all the raw data from the TCP stream and save it into a file called "evidence.zip" which is coincidently also associated with the magic bytes "PK..".



Next I run "Foremost" against this file to extract out the transferred file. A zip file is extracted to the folder "sansevidence".
commandrine@bridge:~$ foremost -i evidence.zip -o sansevidence/
Processing: evidence.zip
|*|
commandrine@bridge:~$
Expanding the archive, I drill down to the folder "word", I find a file called "document.xml".


Opening the file in OpenOffice, the file reveals the following information.
Recipe for Disaster:
1 serving
Ingredients
4 cups sugar
2 cups water
In a medium saucepan, bring the water to a boil. Add sugar.
Stir gently over low heat until sugar is fully dissolved.
Remove the saucepan from heat. Allow to cool completely.
Pour into gas tank. Repeat as necessary.
Calculated the MD5 checksum of the evidence file.
commandrine@bridge:~/word$ md5sum document.xml
90ce695222b157c7148d83e19ea549f6 document.xml
commandrine@bridge:~/word$
Alternatively, I am also able to manually carve out the archive without using "Foremost". I open up the file "evidence.zip" (containing the raw data saved from Wireshark) using Ghex. I delete the ASCII values before the first instance of the ASCII values "Pk.." and delete the chunk starting with "OFT2" at the end of the file.


Once the extra bytes are removed, save the file and it can be opened using any archive management software to reveal the stolen recipe.
wipefox
I got tired of manually keying in commands to wipe my Firefox surfing history and cache so I decided to write my own shell script called "wipefox".
#!/bin/sh
echo “Clearing Firefox surfing history and cache”
sudo srm -rllv .mozilla/firefox/*.default/*.sqlite
sudo srm -rllv .mozilla/firefox/*.default/Cache/*
sudo srm -rllv .mozilla/firefox/*.default/OfflineCache/*
#"wipefox" written by commandrine.
#Please send comments and queries to commandrine[at]gmail[dot]com.
#Version 1.0 dated 4th Sept 2009.
#Pre-requisite is having "secure-delete" installed. Install it using "sudo apt-get install secure-delete".
Lazy to write the script? Download it here.
#!/bin/sh
echo “Clearing Firefox surfing history and cache”
sudo srm -rllv .mozilla/firefox/*.default/*.sqlite
sudo srm -rllv .mozilla/firefox/*.default/Cache/*
sudo srm -rllv .mozilla/firefox/*.default/OfflineCache/*
#"wipefox" written by commandrine.
#Please send comments and queries to commandrine[at]gmail[dot]com.
#Version 1.0 dated 4th Sept 2009.
#Pre-requisite is having "secure-delete" installed. Install it using "sudo apt-get install secure-delete".
Lazy to write the script? Download it here.
Decrypting HTTPS
Had a need to inspect HTTPS to scrutinise application data. Installed ssldump and fired it up.
commandrine@bridge:~$ ssldump -r https.pcap -k server.key -d host 10.10.10.13 > appdata.txt
Enter PEM pass phrase:
commandrine@bridge:~$
Pretty cool stuff. You need the server's private key before you can view session data associated with the said key.
commandrine@bridge:~$ ssldump -r https.pcap -k server.key -d host 10.10.10.13 > appdata.txt
Enter PEM pass phrase:
commandrine@bridge:~$
Pretty cool stuff. You need the server's private key before you can view session data associated with the said key.
Self-signed Digital Certificate
I am currently tinkering with a new pet project. I need a self generated cert for my experiment. I've created a cert using Microsoft's CA offering but it turns out that it is easier to use OpenSSL which is native to Ubuntu. The first step is creating a private key.
commandrine@bridge:~$ openssl genrsa -des3 -out server.key 1024
Generating RSA private key, 1024 bit long modulus
.............................................++++++
...................++++++
e is 65537 (0x10001)
Enter pass phrase for server.key:
Verifying - Enter pass phrase for server.key:
commandrine@bridge:~$
Next step is generating the test cert.
commandrine@bridge:~$ openssl req -new -x509 -key server.key -out cacert.pem -days 1095
Enter pass phrase for server.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:SG
State or Province Name (full name) [Some-State]:Singapore
Locality Name (eg, city) []:Singapore
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Security Republic
Organizational Unit Name (eg, section) []:Information Security
Common Name (eg, YOUR name) []:commandrine
Email Address []:commandrine@gmail.com
commandrine@bridge:~$
Hmmmm. Turns out that IIS only accepts PKCS format certs. Had to convert my cert before I could import it.
commandrine@bridge:~$ openssl pkcs12 -export -passout pass:"testing" -inkey server.key -in cacert.pem -out cacert.p12 -name "cacert"
Enter pass phrase for server.key:
commandrine@bridge:~$
commandrine@bridge:~$ openssl genrsa -des3 -out server.key 1024
Generating RSA private key, 1024 bit long modulus
.............................................++++++
...................++++++
e is 65537 (0x10001)
Enter pass phrase for server.key:
Verifying - Enter pass phrase for server.key:
commandrine@bridge:~$
Next step is generating the test cert.
commandrine@bridge:~$ openssl req -new -x509 -key server.key -out cacert.pem -days 1095
Enter pass phrase for server.key:
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [AU]:SG
State or Province Name (full name) [Some-State]:Singapore
Locality Name (eg, city) []:Singapore
Organization Name (eg, company) [Internet Widgits Pty Ltd]:Security Republic
Organizational Unit Name (eg, section) []:Information Security
Common Name (eg, YOUR name) []:commandrine
Email Address []:commandrine@gmail.com
commandrine@bridge:~$
Hmmmm. Turns out that IIS only accepts PKCS format certs. Had to convert my cert before I could import it.
commandrine@bridge:~$ openssl pkcs12 -export -passout pass:"testing" -inkey server.key -in cacert.pem -out cacert.p12 -name "cacert"
Enter pass phrase for server.key:
commandrine@bridge:~$
Encrypted?
 It is curious that LogMeIn doesn't require a user to enter their LogMeIn profile information during installation... yet the installed client knows which account it is associated with.
It is curious that LogMeIn doesn't require a user to enter their LogMeIn profile information during installation... yet the installed client knows which account it is associated with.This piqued my interest and I took a peek at the installer file. It seems that LogMeIn uses a VeriSign digitial certificate to encrypt information within the installer?
UPX discovery
 Packers are tools used to compress executables to reduce their file size whilst retaining their executable property. Hackers harness packing as one of the numerous tricks to avoid detection. However, there are times when software authors pack their legitimate tools and thus not all packed executables are malware.
Packers are tools used to compress executables to reduce their file size whilst retaining their executable property. Hackers harness packing as one of the numerous tricks to avoid detection. However, there are times when software authors pack their legitimate tools and thus not all packed executables are malware.UPX is a popular packer. I packed several files with it and analysed them in a hex editor to try to discover patterns. Lo and behold... the tell-tale signs of a UPX packed file is the presence of UPX strings (ie. UPX0, UPX1 and UPX!).
Further investigation demonstrates that searching for UPX strings is not accurate because the UPX packed executables still function even if you change the UPX text. A reliable methodology of detecting packed executables is a tool called PEiD. It identifies UPX packed files by hexadecimal values.


Subscribe to:
Comments (Atom)
Ubuntu maintenance script
Wrote a simple script for keeping packages and snaps updated in Ubuntu.
-
This annoying message popped up after I ran the update in avast! in Ubuntu yesterday. avast! crashes every time I attempt to launch it after...
-
I decided to install a digital certificate for my Gmail account. This is simple and free to set up. Apply for a free certificate from Comod...





