Searching for strings matching "aol.com" reveals "AUTH=LOGIN". I locate the login sequence in Wireshark.
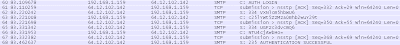 I figure that the string "VXNlcm5hbWU6" is encoded and has signficance. Googling this string reveals that it is "Username:" encoded in Base64. I use the "Enocde/Hash" tool in Paros (Windows) to confirm this fact. Lo and behold! I start to decode the other encoded strings to reveal the password "558r00lz".
I figure that the string "VXNlcm5hbWU6" is encoded and has signficance. Googling this string reveals that it is "Username:" encoded in Base64. I use the "Enocde/Hash" tool in Paros (Windows) to confirm this fact. Lo and behold! I start to decode the other encoded strings to reveal the password "558r00lz".



To locate the attachment that Ann sent, I search for the string "Content-Type:". The name of the attachment is "secretrendezvous.docx". I usually like to challenge myself by manually carving out file transfers but in this specific case, I was unsuccessful. Using file carvers like "tcpxtract" and "Foremost" also resulted in failure. I resorted to using NetMiner (Windows) to acquire this file.
 I do not have Office 2007 installed on my laptop. I decided to be creative and viewed the file in Google Docs to reveal their secret meeting place. The MD5 hash of this file is "9e423e11db88f01bbff81172839e1923". To access the embedded image, I rename the extension ".docx" to ".zip". I am able to access the image from the "/word/media/" folder. The MD5 hash of this image is "aadeace50997b1ba24b09ac2ef1940b7".
I do not have Office 2007 installed on my laptop. I decided to be creative and viewed the file in Google Docs to reveal their secret meeting place. The MD5 hash of this file is "9e423e11db88f01bbff81172839e1923". To access the embedded image, I rename the extension ".docx" to ".zip". I am able to access the image from the "/word/media/" folder. The MD5 hash of this image is "aadeace50997b1ba24b09ac2ef1940b7".


No comments:
Post a Comment