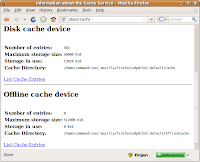
 Locate your Firefox cache by entering "about:cache" in your browser address bar.
Locate your Firefox cache by entering "about:cache" in your browser address bar.Note: The cache folder location (eg. u0p8r5n2.default) is randomly generated and different from system to system.
Navigate to both "Cache" and "OfflineCache" folders to wipe by running the "sudo srm -rllv *" command.
There are other traces of your surfing history (eg. search keywords, files downloaded, URLs entered) stored by your browser. To wipe these, navigate to your cache folder and securely delete all files with the extension .sqlite.
commandrine@bridge:~/.mozilla/firefox/u0p8r5n2.default$ sudo srm -rllv *.sqlite
Using /dev/urandom for random input.
Wipe mode is insecure (one pass [random])
Wiping content-prefs.sqlite * Removed file content-prefs.sqlite ... Done
Wiping cookies.sqlite * Removed file cookies.sqlite ... Done
Wiping downloads.sqlite * Removed file downloads.sqlite ... Done
Wiping formhistory.sqlite * Removed file formhistory.sqlite ... Done
Wiping permissions.sqlite * Removed file permissions.sqlite ... Done
Wiping places.sqlite * Removed file places.sqlite ... Done
Wiping search.sqlite * Removed file search.sqlite ... Done
Wiping urlclassifier3.sqlite * Removed file urlclassifier3.sqlite ... Done
commandrine@bridge:~/.mozilla/firefox/u0p8r5n2.default$
Wipe mode is insecure (one pass [random])
Wiping content-prefs.sqlite * Removed file content-prefs.sqlite ... Done
Wiping cookies.sqlite * Removed file cookies.sqlite ... Done
Wiping downloads.sqlite * Removed file downloads.sqlite ... Done
Wiping formhistory.sqlite * Removed file formhistory.sqlite ... Done
Wiping permissions.sqlite * Removed file permissions.sqlite ... Done
Wiping places.sqlite * Removed file places.sqlite ... Done
Wiping search.sqlite * Removed file search.sqlite ... Done
Wiping urlclassifier3.sqlite * Removed file urlclassifier3.sqlite ... Done
commandrine@bridge:~/.mozilla/















