Technology is never foolproof and here is an excellent example where common sense is overwhelmingly essential.
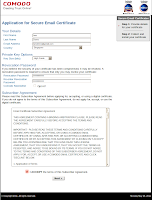
Technology is never foolproof and here is an excellent example where common sense is overwhelmingly essential.I received the highlighted link in my Gmail which wasn't marked as spam. A quick glance at the path and I knew this was obviously a ruse but I wondered why Gmail's spam detection didn't pick this up. I quickly ran the suspicious link against the scanners hosted on VirusTotal and was utterly disappointed that not a single engine was able to mark it as malicious.