I always preach about the dangers of revealing too much information. I like this article because it provides a simple example to reinforce my point. Discretion is the key.
Researchers develop a Proof-of-concept attack that uncovers the identity of web surfers based on their social networking activities.
The economics of malware
 Interesting read about the driving force behind malware writing and distribution.
Interesting read about the driving force behind malware writing and distribution.Whilst we are on the topic of malware... malicious PDF installs backdoor on victim’s system and dials home to Singapore hosted server*. Nice!!!
Anyone wants to call Alan to give him the bad news?
* First came across this cool story on werew01f's blog.
Network forensics puzzle #4
Puzzle #4 is out. I've been pre-occupied and exhausted by work thus the delay in posting my answers for puzzle #3.
The answers for the first 2 answers were straight forward enough.
1) 00:25:00:fe:07:c4
2) AppleTV/2.4
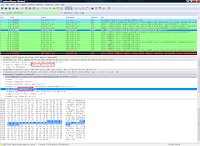
The search terms (ie. questions 3 and 8) were a bit tedious to find manually by combing through Wireshark but easier in NetworkMiner. Alternatively, searching using "ngrep" on Ubuntu was pretty painless. The 2 movies that Ann clicked on are also listed in NetworkMiner.
3) h, ha, hac, hack
4) Hackers
6) Sneakers
8) iknowyourewatchingme



Answers to questions 5 and 7 courtesy of NetworkMiner.
5) http://a227.v.phobos.apple.com/us/r1000/008/Video/62/bd/1b/mzm.plqacyqb..640×278.h264lc.d2.p.m4v
7) $9.99



The answers for the first 2 answers were straight forward enough.
1) 00:25:00:fe:07:c4
2) AppleTV/2.4

The search terms (ie. questions 3 and 8) were a bit tedious to find manually by combing through Wireshark but easier in NetworkMiner. Alternatively, searching using "ngrep" on Ubuntu was pretty painless. The 2 movies that Ann clicked on are also listed in NetworkMiner.
3) h, ha, hac, hack
4) Hackers
6) Sneakers
8) iknowyourewatchingme



Answers to questions 5 and 7 courtesy of NetworkMiner.
5) http://a227.v.phobos.apple.com/us/r1000/008/Video/62/bd/1b/mzm.plqacyqb..640×278.h264lc.d2.p.m4v
7) $9.99



Subscribe to:
Comments (Atom)
Ubuntu maintenance script
Wrote a simple script for keeping packages and snaps updated in Ubuntu.
-
This annoying message popped up after I ran the update in avast! in Ubuntu yesterday. avast! crashes every time I attempt to launch it after...
-
I decided to install a digital certificate for my Gmail account. This is simple and free to set up. Apply for a free certificate from Comod...
