Malware exploit the fact that your machines will follow instructions stored in a hidden text file called "autorun.inf". The sample below basically instructs your machine to execute the file "setup.exe" when the CD is read by your CD-ROM.
[AutoRun]
open=setup.exe
icon=setup.exe,0Having the "Autorun" feature in this scenario is convenient because the installer file will be triggered upon insertion of the installation CD. Imagine if a hacker planted a Trojan on a USB flash drive. How convenient would that be now?
Do not panic! There is hope. Modifying your
registry within XP permits you to disable "Autorun".
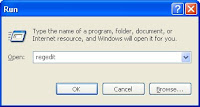
- Access your registry by clicking on your "Start" button then "Run". Type in "regedit" before clicking "OK".
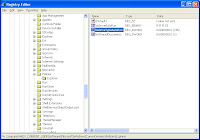
- Expand "HKEY_CURRENT_USER" followed by "Software", "Microsoft", "Windows", "CurrentVersion", "Policies" then "Explorer".
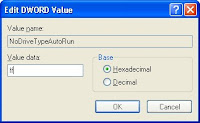
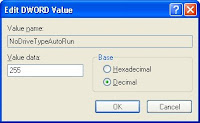
- Double click the entry "NoDriveTypeAutoRun".
- Change the value to "ff" (Hexadecimal) or "255" (Decimal) then click "OK".
- Restart your machine for the change to take effect.
 Note:
Note: This registry change is only relevant to the current user you are logged in as. To disable "autorun" for the entire machine, you would want to change the value in "HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer\NoDriveTypeAutoRun" instead. You have to manually create this entry if it cannot be found in your registry. It is advisable to backup your registry before attempting any modifications.
"Autoplay" was a feature introduced in XP and has been included in Windows OSs since. It serves a similar function to "Autorun" but invokes a menu on top of executing the "autorun.inf" instructions. To disable "Autoplay" in XP:
- Click "Start", "Run" then enter "gpedit.msc".
- The "Group Policy" configuration window will appear. Drill down to "Computer Configuration", "Administrative Templates" and "System".
- Double-click "Turn autoplay off" listed in the right panel.
- The default setting is "Not configured" . Set it to "Enabled" and select "All drives".